5 Cybersecurity Trends to Watch in 2022

For this week’s Tuesday Tech Tip. We’re going to talk about the 5 biggest cybersecurity trends that are expected in 2022 as it relates to cybercriminals.
Hospital Ransomware Attack Turns Deadly

Ransomware attacks have been a costly threat to companies and computer systems for years. Now, these malicious attacks are upping the ante by targeting hospitals and healthcare facilities – a dangerous crime that may have deadly consequences. According to a lawsuit filed against Springhill Medical Center, a 2019 ransomware attack that crippled hospital computer systems […]
Local IT Firm Guarantees Gulf Coast Organizations Protection From Ransomware And Security Threats Through A Multi-Layer Security Approach

LOCAL IT FIRM GUARANTEES GULF COAST ORGANIZATIONS PROTECTION FROM RANSOMWARE AND SECURITY THREATS THROUGH A MULTI-LAYER SECURITY APPROACH Robertsdale, AL (March 15, 2018) – Business Information Solutions (BIS) launches one-of-a-kind security program for small to medium sized businesses called BIS Advanced Cybersecurity Threat Protection. This new solution provides organizations with a multi-layered, defense-in-depth approach to […]
5 Ransomware Statistics Every Business Owner Needs to Know

While ransomware statistics in 2017 were alarming in terms of growth and severity of attacks, the cybersecurity industry has made great strides in defending against them. But despite our best efforts, the threat shows no signs of going away.
4 Cyber Security Predictions for 2018

If 2017 has shown us anything, it’s that even major organizations can come to a grinding halt due to cyber security attacks. This message probably won’t come as a surprise to many businesses. After all, several big-name brands have suffered embarrassing data breaches in recent years, causing significant financial and reputational damage. What makes this […]
Check the list of free ransomware decryptors

We’ve gotten so caught up discussing ransomware prevention with our clients that we’ve neglected to mention that several strains have already been defeated. In fact, there’s a decent chance you can actually decrypt all your data for free. Always make sure to check these lists before responding to a cyber attacker’s demands. The state of […]
The Anatomy of a Crypto–Ransomware Attack And How to Prevent Them
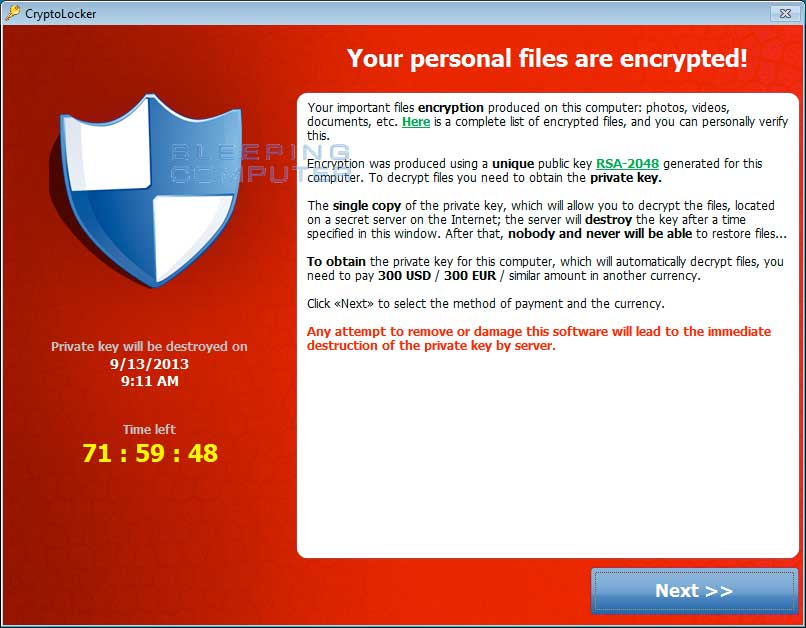
Almost every day there is a big corporation that is getting hit by one of the variance of the Crypto – Ransomware malware. For every big case that makes the news there are thousands of others that are being affected. These attacks are not going away anytime soon.










