
Top 5 IT Projects to Tackle During Summer Slowdowns
Summer is often a quieter season for many businesses. With employees taking vacations and fewer meetings on the calendar, this mid-year lull presents the perfect
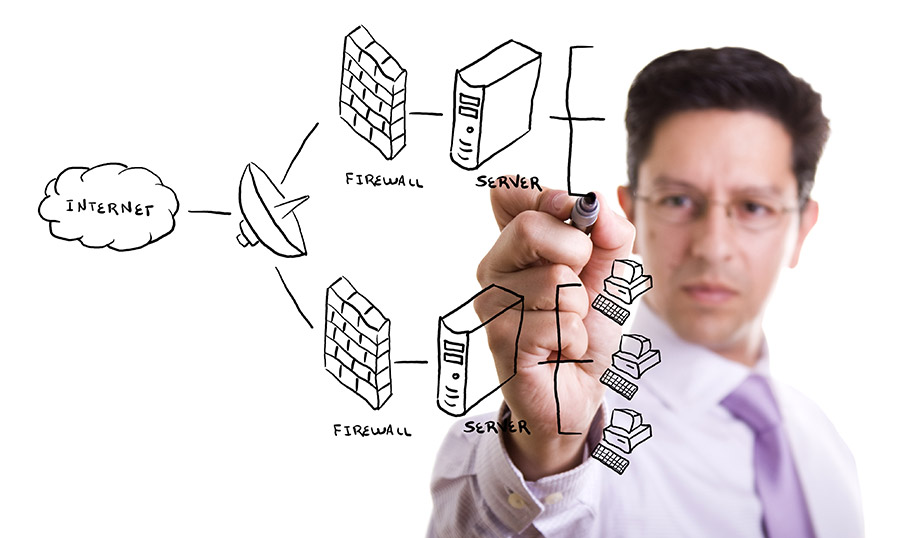
According to the 2015 Cyberthreat Defense Report, over 70% of businesses have reported falling victim to a successful cyberattack in the last 12 months. At BIS we take a comprehensive layered network security approach. Our solution employs multiple vendors security definitions. Our network security solutions will help to prevent security threats from infiltrating your network by scanning for vulnerabilities, filtering website traffic, tracking system changes and alerting if any threats are found.





















With the 24 hour sentinel monitoring, I can sit back and wait on Business Information Solutions to tell me if something needs to be upgraded or if a backup fails. I’m no longer constantly checking for errors and problems on our network and servers.

BIS has made it where I’m not the one having to go around checking each machine to make sure it meets HIPAA laws. That’s what I have BIS for!

Staff morale has gone up because I receive less complaints about our network.

We’ve saved 40-50 hours per month on inside labor since we no longer have to figure out the problem and learn how to fix it.

I don’t know where we would be if Business Information Solutions was not monitoring our system or us. Since going with them, we’ve had NO CRASHES.

With the IT services that Business Information Solutions provides, we no longer have to worry about being ‘down’ for hours or days with issues. Calls and work orders are responded to very quickly and efficiently.





Other Security Services: Desktop Security | Network Security | Mobile Device Security | Proactive Management | Video Surveillance | Security & Compliance Training

Summer is often a quieter season for many businesses. With employees taking vacations and fewer meetings on the calendar, this mid-year lull presents the perfect

The clock is ticking. Microsoft has officially announced that Windows 10 will reach end of support on October 14, 2025. That’s just a few short

Non-profits are built to serve missions, not to fight cybercrime—but in today’s digital world, that’s no longer optional. Cybersecurity attacks are increasingly targeting non-profit organizations,

Remote work is here to stay—and for business owners in Robertsdale and Baldwin County, that means adjusting your operations to support a workforce that isn’t

Protecting Your Business in Mobile, AL, Pensacola, FL, and Beyond As cyber threats continue to rise, compliance with the Cybersecurity Maturity Model Certification (CMMC) is

The Gulf Coast region—home to bustling cities like Pensacola, Mobile, Baldwin County, and Biloxi—is no stranger to hurricanes and tropical storms. These powerful storms can
See What Our Clients Are Saying About BIS