The Anatomy of a Crypto–Ransomware Attack And How to Prevent Them
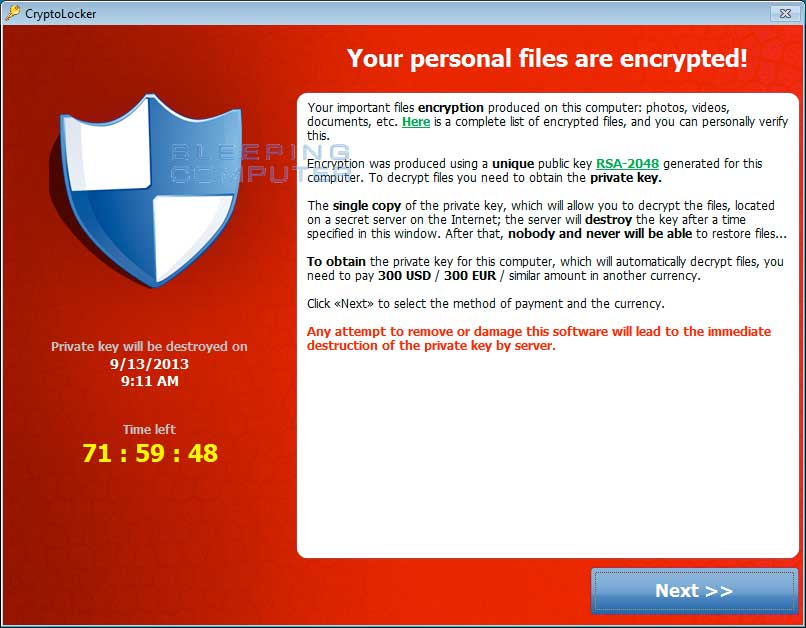
Almost every day there is a big corporation that is getting hit by one of the variance of the Crypto – Ransomware malware. For every big case that makes the news there are thousands of others that are being affected. These attacks are not going away anytime soon.
9 Steps to an Effective Cyber Security Plan

There is not a day that goes by that you do not read in the paper or hear on television that some company has been the victim of Cyber Crime. The alarming thing is that for every incident that you hear about there are probably six more that have happened that you don’t hear about. […]
How Safe is Your Password Really?

Imagine this: You’re setting up your login information for your email, or maybe it’s your Cloud database account. Upon entering your password, the program prompts you to include a capitalized letter, number and possibly a symbol in your password. You wonder, “Is this really necessary? Who’s going to be THAT determined to break into my […]
Apple Devices Can Get Viruses

Are you under the impression Apple devices are exempt from viruses and hacking? A great deal of Apple users consider Apple systems safer to use than Windows because of the “built-in” security Apple programs into their devices. But Windows operating systems also come with similar existing security to prevent hackers and viruses. So why is […]
Must Know Info For Backup, Security and Disaster Recovery

The Importance of a Proactive, NOT Reactive Approach With the major role information technology plays in the way business is conducted in today’s world, it’s crucial that every business owner, both large and small, be able to see the big picture of protecting client and company data from disaster. Data backup disaster comes in many […]
Are You Protected From A Data Backup Disaster?

What Are You Waiting For? When it comes to protecting the critical files and documents for your business or company, are you taking the necessary precautions? Many small to medium sized businesses are faced with the same problem when it comes to data backup, and that problem is that they haven’t done anything to prepare […]
Is Your BYOD Policy HIPAA Compliant?

Bring Your Own Device or BYOD policies are a great tools for employees and a money saver for companies, but it can also be a risky policy if not conducted properly. Mobile devices and a BYOD policy in the health care field can allow professionals to easily transition workflows, boost productivity and improve communication. The […]
Is Working on Personal Devices Risky Business?

It’s natural and common for your employees to want to conduct some of their work at home or on the road, and often the most convenient way is to do so on their personal devices. However, this could be putting your business at risk, and thus allowing your employees to conduct their work on personal […]
Tips to Sink ATM Skimming
Today’s world is far from the wild west, but bank robbers are still rampant and constantly after your money. The only difference is there tactics are far more technologically advanced. Criminals gain access to your bank account via ATM machines and some sneaky skimming of your money. These criminals use a combination of advanced card […]










