Ransomware Recent Activity
Almost every day there is a big corporation that is getting hit by one of the variance of the Crypto – Ransomware malware. For every big case that makes the news there are thousands of others that are being affected. These attacks are not going away anytime soon. More and more devices are connected daily. Tablets, wearable devices, the Internet of Things (iOT), the overall global public cloud market size; to name a few. This is one of the biggest threats to business today. It affects businesses in the following ways:
- Inability to service their clients
- Reputation Damage
- Massive loss of revenue
If the large corporations with large IT budgets are not able to secure their networks, how is the standard small and midsize company ever going to be protected? That is the question that I have spent many hours trying to confidently answer. The good news is we are finding success with a particular security formula.
To begin I think it is important that we understand the anatomy of a Crypto – Ransomware attack. Below is a standard model for how these attacks take place. Note there are other ways that are taking place but this is by far the most common.
Installation. The victim’s computer gets infected. Usually this takes place via some form of phishing email link. These types of attacks are often targeted to certain individuals based on their position with the company or through hacking of someone else’s account that the individual might trust. These are referred to as “targeted phishing attacks”. Next, the malicious code installs itself, and sets keys in the Windows Registry to start automatically every time the computer boots up.
Contacting Headquarters. Before the Crypto – Ransomware code can execute, it contacts the criminal’s server via the Internet. This is referred to as the malware “phoning home”.
Handshake and Keys. The Ransomware client and server identify each other through a carefully arranged “handshake” and the server generates to cryptographic keys. One key is kept on your computer; the second key is stored securely on the criminal server.
Encryption. With the cryptographic keys established, the Ransomware on your computer starts encrypting every file that it finds with any of dozens common file extensions. From Microsoft Office documents to Adobe PDF documents to image files and more.
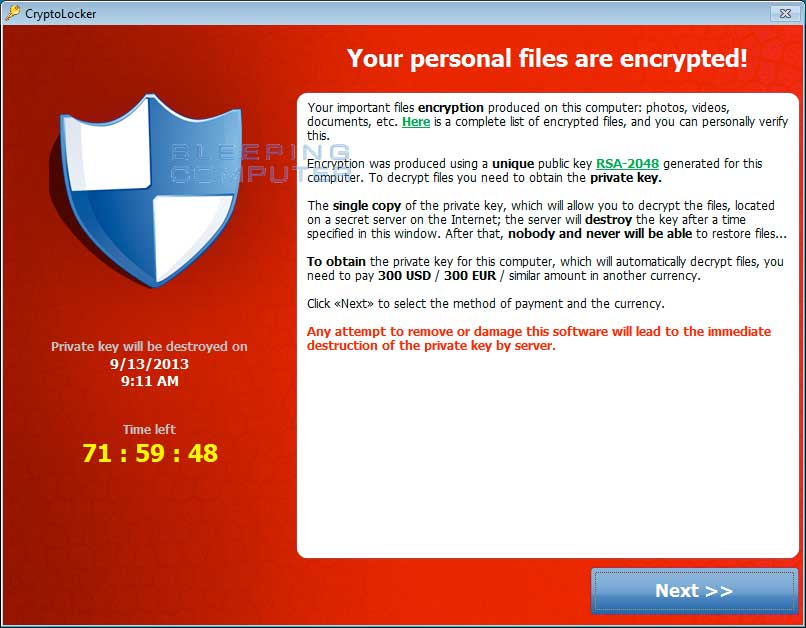
Extortion. The Ransomware displays the screen giving you a time limit to pay the criminals before the criminals destroy the key that will decrypt your files. At this point, you are at the mercy of these criminals. They type of encryption is the industry standard and even with the fastest computer would take 10,000 years to crack.
Disruption of the Crypto – Ransomware Attack
The solution to this problem requires a multi-layered security approach. There are approximately 82,000 new Malware threats created every day. The list of threats is so long and so complex that no one security solution has them all covered. Below is a listing of what we feel like is the security formula needed to protect small to midsize businesses.
- Security and Compliance Training. IBM did a study in 2015 that revealed that 95% of all breaches were caused by people. People need to be trained on how to recognize threats and what to do when they see one. Companies also need to have proper policies that protect themselves from law suits and compliance violations in the event a breach occurs.
- Email Security. Email is by far the largest means for criminals to infect computer networks. It is important to be held to control the employees access to non business related email accounts. It is also important to have a comprehensive SPAM Firewall that can block SPAM as well as allow for the ability to send encrypted Email for sensitive data.
- Network Security. The ultimate goal for the criminal is to infect not just one machine but the entire network environment. A big challenge in today’s environment is the number of devices as well as the amount of work and data that is happening while not in the office. A company needs to be able to control the Account logins, overall network traffic, block malicious code, filter Internet traffic as well as allow for secure access from outside the office.
- Desktop Security. In many small to midsize business environments this is the only form of protection. Often the product chosen does not cover much of the overall threat. Commonly referred to as Antivirus; this product needs to do the following: antivirus and anti-spyware protection, USB device management, Crypto Prevention capabilities, and automatic alerting to the network administrator if an infection happens or the product is not performing properly.
- Mobile Device Security. In 2015 approximately 40% of all breaches occurred from mobile devices. A good product contains the following. AES 256 Bit Encryption, mobile password management, remote data wiping, geolocation, USB Encryption management and functionality across all platforms
- Proactive IT Management. One of the biggest challenges is to always be on guard. In today’s environment it is impossible to humanly provide the level of IT Management without comprehensive “tools”. These tools must do the following. Automated Microsoft Patching, Automated Application Patching For other applications such as Adobe, Chrome, Flash, GoToMeeting, and 150 other commonly used software’s. These “tools” also watch for new User Account creation, new software installation or removal, monitoring of rogue services as well as keep the system running optimally.
- Cloud Based Data Recovery/Business Continuity Solution. One of the best offenses is a great defense. In the event that a Ransomware attack is successful, the most important thing is to have a recent copy of your data readily available. An important part of a good Data Recovery plan is understanding how long you can be without the data as well as how often the data is backed up. For example, could you be without your data for 2 to 3 days in the event your server went down? Or could you reproduce all of the daily transactions if your server went down at 4 PM in the afternoon and the backup happened at midnight the previous day. There is a great article in our January newsletter that digs into what a good backup looks like.
We have worked diligently in this multilayered approach and have found a lot of success. I hope this information can be helpful to your organization. I’m always available to answer any questions are dig deeper into a solution that would suit your business. Thanks so much for reading our blog.
Respectfully,
Phillip D. Long
CEO
plong@askbis.com
Business Information Solutions, Inc.
For more information about Business Information Solutions please visit the BIS Website. BIS, Inc. provides Network Consulting and Proactive IT Support for businesses in Gulfport and Biloxi MS, Mobile, Daphne, Spanish Fort, Fairhope, Foley AL and Pensacola FL.