
You can’t manage what you can’t see. Even a small network generates over 250,000 logs per hours. An impossible task for a human to review. We now live in the days of sophisticated digital hackers so your concern shouldn’t be if you’re going to get hacked, but what you’re going to do when it happens.

We’ve all had a relationship go sour over time, a communication breakdown if you will. Here are 4 tips to keep communications flowing throughout the

Technology has become so richly interwoven into the fabric of our lives it would be hard to imagine doing some of our most common tasks

Introduction What would an hour of downtime cost your business? As a business owner, I’ve had many slick salespeople try to convince me of things

HIPAA Audits – The Wait is Over – It’s Real This Time As an IT professional, there are several things that always keep you up
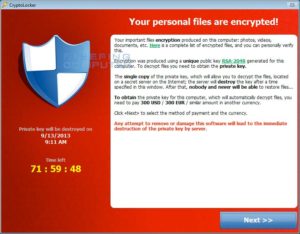
Almost every day there is a big corporation that is getting hit by one of the variance of the Crypto – Ransomware malware. For every big case that makes the news there are thousands of others that are being affected. These attacks are not going away anytime soon.

This blog is designed to further explain The Theory of Constraints and define some of the processes and applications for discovering and solving the constraints in a business setting.

In today’s environment, the core of any security strategy needs to shift from breach prevention to breach acceptance.” – Gemalto, data security firm Times they

One of the biggest challenges for any entrepreneur or business person is what Gino Wickman; author of the book Traction, calls “Letting go of the

There is not a day that goes by that you do not read in the paper or hear on television that some company has been
Artificial intelligence tools like Microsoft Copilot are quickly becoming part of everyday business workflows. They help employees work faster, summarize information, and make sense of

As organizations continue to adopt artificial intelligence, many are looking beyond productivity use cases and toward internal operations. Human Resources is one of the most

FOR IMMEDIATE RELEASE Robertsdale, AL – January 2026 – Business Information Solutions, Inc. (BIS), a technology solutions provider serving businesses across the Gulf Coast, has
Microsoft Copilot and AI-powered tools promise to transform how work gets done. However, AI does not create structure where none exists. It amplifies what is

Cyber incidents over the past year have made one thing clear. Breaches are rarely random. When recent attacks are examined together, consistent patterns emerge that

From fake websites and phishing emails to payment fraud and counterfeit listings, online shopping scams are on the rise. Both businesses and consumers play a

When a cyber incident strikes, every minute counts. Whether it’s ransomware, a phishing attack, or a data breach, how a business responds in the first

October’s spooky season offers a fitting backdrop for a review of recent cyber horror stories. Business owners must recognize that cyber threats are not fictional

Cyber threats are no longer limited to large corporations. In fact, small businesses are now prime targets due to limited security resources and valuable data.

Nonprofit organizations often run on lean budgets. Every dollar is carefully allocated to programs and services, but technology expenses are sometimes overlooked or mismanaged. These